It is important to realize that your WiFi Network does not end at your home walls. It is possible for the network to extend over 300 feet through the air. If your wireless access point is not properly secured, people from other homes, offices or nearby buildings can gain access to it. Even a passwrby can get access to your network by using free mobile apps that can scan for unsecured networks. It is vital that you take proper preventative measures in securing the device to protect your network. People who are able to connect to your wireless router or network may be able to do the following:
Most people connect to the wireless network utilizing their mobile devices, such as Smartphones, tablets, Smart tv and laptops, as it is not exactly practical to switch off their wifi access. Below you will find tips on how to ensure that your IT network is more secure:
Use WiFi Protected Access (WPA)
Wired Equivalent Privacy (WEP) standard of security is old & broken, which means that hackers can easily break into the WEP-protected network utilizing a hacking method such as Aircrack--ng. To avert hackers from accessing your WiFi Network, it is vital that you use some form of deviation like WiFi Protected Access (WPA) protection. Either the WPA or the recent WPA2 standard is ideal.
Utilize A Secure WPA Passwordsecure Wifi
It is recommended to create a randomly long password or passphrase to protect your wireless network. The randomly long password or passphrase can make it difficult for intruders to hack into your network. Take the time to test the security of the WPA protected network by using a service like CloudCracker.
In order for the test to succeed, you should not reveal your password/passphrase. Once this is done, you will be asked to provide some data/information (typically data/information that hackers could capture via a device from anywhere within the range of your WiFi Network). The service will do everything to extract your password or passphrase.
Check For Rogue WiFi Access Points
Rogue wireless access points tend to present a huge security threat. These are not your authorized wireless access points, but the ones that have been brought in by visitors, your computer technician who knows your password or possibly by intruders who have clandestinely connected to one, for instance a wired Ethernet port, and concealed it.
Make A Separate Network Available for Guests
If you have visitors and allow them to use your WiFi Network on a regular basis, it is highly recommended that you provide a separate network for the guests. This means that your guests can still connect to the Internet, but without accessing your primary internal network. This is usually practiced regularly for security purposes and to prevent their guests from unintentionally infecting their primary network with viruses or malware.
Is someone using my wifi network?
- Access your computer & view all the files on your computer or spread a virus
- View all the websites that you visit, read all your emails as they travel through the network, copy your log-in names and passwords using a hidden software and then hack into your accounts bank account
- Slow down your computer or laptop and the Internet connection speed
- Send spam and/or perform illegal activities like hacking, so threat/hate messaging using your Internet connection
Most companies and individuals go to great lengths to ensure that unauthorized users cannot access their WiFi Network. However, wireless access points can provide hackers with a few convenient ways to access it. This is because wifi signals are frequently broadcasted past the walls of the company and throughout the immediate area, enticing the hackers to get in.
Most people connect to the wireless network utilizing their mobile devices, such as Smartphones, tablets, Smart tv and laptops, as it is not exactly practical to switch off their wifi access. Below you will find tips on how to ensure that your IT network is more secure:
Use WiFi Protected Access (WPA)
Wired Equivalent Privacy (WEP) standard of security is old & broken, which means that hackers can easily break into the WEP-protected network utilizing a hacking method such as Aircrack--ng. To avert hackers from accessing your WiFi Network, it is vital that you use some form of deviation like WiFi Protected Access (WPA) protection. Either the WPA or the recent WPA2 standard is ideal.
Utilize A Secure WPA Passwordsecure Wifi
It is recommended to create a randomly long password or passphrase to protect your wireless network. The randomly long password or passphrase can make it difficult for intruders to hack into your network. Take the time to test the security of the WPA protected network by using a service like CloudCracker.
In order for the test to succeed, you should not reveal your password/passphrase. Once this is done, you will be asked to provide some data/information (typically data/information that hackers could capture via a device from anywhere within the range of your WiFi Network). The service will do everything to extract your password or passphrase.
Check For Rogue WiFi Access Points
Rogue wireless access points tend to present a huge security threat. These are not your authorized wireless access points, but the ones that have been brought in by visitors, your computer technician who knows your password or possibly by intruders who have clandestinely connected to one, for instance a wired Ethernet port, and concealed it.
Make A Separate Network Available for Guests
If you have visitors and allow them to use your WiFi Network on a regular basis, it is highly recommended that you provide a separate network for the guests. This means that your guests can still connect to the Internet, but without accessing your primary internal network. This is usually practiced regularly for security purposes and to prevent their guests from unintentionally infecting their primary network with viruses or malware.
Is someone using my wifi network?
- SoftPerfect WiFi Guard is basic version of the SoftPerfect Network Scanner which is more suited for detecting unknown or unauthorized network connections. Good this about this tool is that it will scan your network for connected devices and re-scan every xx minutes, popping up a message if an unknown connection has been found. This is my favorite tool

- Wireless Network Watcher is one of his many utilities that can tell you who all are using your wifi network. The good thing is it requires no setting up of IP address ranges and starts scanning your main network adapter automatically for connected devices.
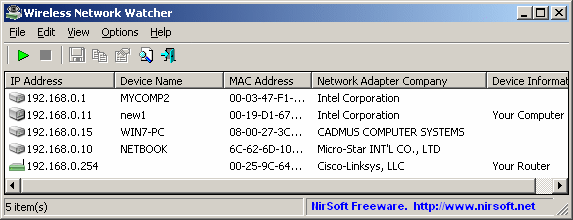
- Advanced IP Scanner is an all round network administration tool that can do a number of tasks in addition to scanning your network for connections. There’s also remote options to Wake-on-LAN and shutdown, connect via HTTP/FTP as well as remote control with Remote Desktop. These features are unnecessary for simply scanning your network for wireless connections so you can ignore them.

<Last updated Jan 2017>

